Description of procedures for digital meetings for Mid Sweden University staff
This procedure is part of Mid Sweden University’s management information system for information security. The purpose of the procedures is to facilitate the choice of technology solution for the digital meeting based on the content.
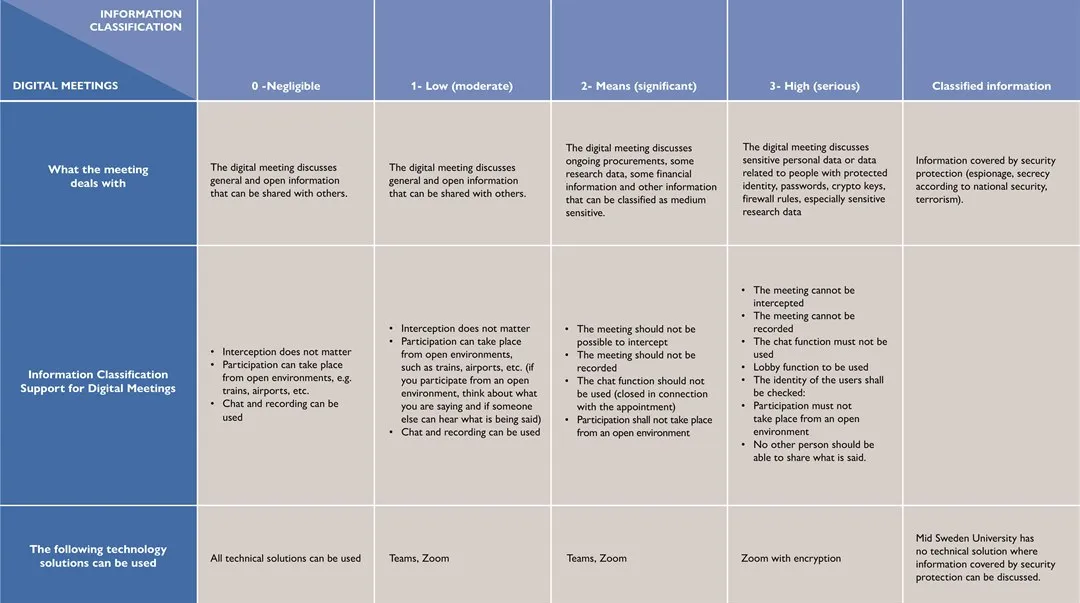
Mid Sweden University’s routine description for digital meetings
The FAQ below “What the meeting deals” describes which technical solutions can be used for digital meetings based on the content of the meeting. The choice of technical solution is based on an information classification. A confidentiality value (K-value) is associated with each type of information processed at the meeting.
-
General and open information — negligible
What the meeting deals with
The digital meeting discusses general and open information that can be shared with others.
K-value: 0 — negligible
Information Classification Support for Digital Meetings
- Interception does not matter
- Participation can take place from open environments, e.g. trains, airports, etc.
- Chat and recording can be used
The following technology solutions can be used
All technical solutions can be used
-
General and open information — Low (moderate)
What the meeting deals with
The digital meeting discusses general and open information that can be shared with others.
K-value: 1 — Low (moderate)
Information Classification Support for Digital Meetings
- Interception does not matter
- Participation can take place from open environments, such as trains, airports, etc. (if you participate from an open environment, think about what you are saying and if someone else can hear what is being said)
- Chat and recording can be used
The following technology solutions can be used
Teams, Zoom
-
Information on research data, procurements, etc. — Means (significant)
What the meeting deals with
The digital meeting discusses ongoing procurements, some research data, some financial information and other information that can be classified as medium sensitive.K-value: 2 — means (significant)
Information Classification Support for Digital Meetings
- The meeting should not be possible to intercept
- The meeting should not be recorded
- The chat function should not be used (closed in connection with the appointment)
- Participation shall not take place from an open environment
The following technology solutions can be used
Teams, Zoom
-
Sensitive personal data and research data — High (serious)
What the meeting deals with
The digital meeting discusses sensitive personal data or data related to people with protected identity, passwords, crypto keys, firewall rules, especially sensitive research data
K-value: 3 — High (serious)
Information Classification Support for Digital Meetings
- The meeting cannot be intercepted
- The meeting cannot be recorded
- The chat function must not be used
- Lobby function to be used
- The identity of the users shall be checked:
- Participation must not take place from an open environment
- No other person should be able to share what is said.
The following technology solutions can be used
Zoom with encryption — instruction for activation
-
Classified information
Information covered by security protection (espionage, secrecy according to national security, terrorism).
Mid Sweden University has no technical solution where information covered by security protection can be discussed.