Description of procedures for digital workspaces for Mid Sweden University staff
This procedures is part of Mid Sweden University's management information system for information security. The purpose of the procedures is to make it easier for the end user to choose the right workspace for their digital information, depending on the type of information.
Preservation and sorting out
No information is archived / preserved in the long term via reported workspaces. Documents that are to be archived are handled in the business systems and processes to which they belong and are archived electronically, or alternatively submitted digitally or on paper to the university's archive function for archiving according to agreed routines. This does not constitute an obstacle to handling copies of archived information / information that will be archived via the workspaces when needed, routines in the established guides also apply to copies of archived information.
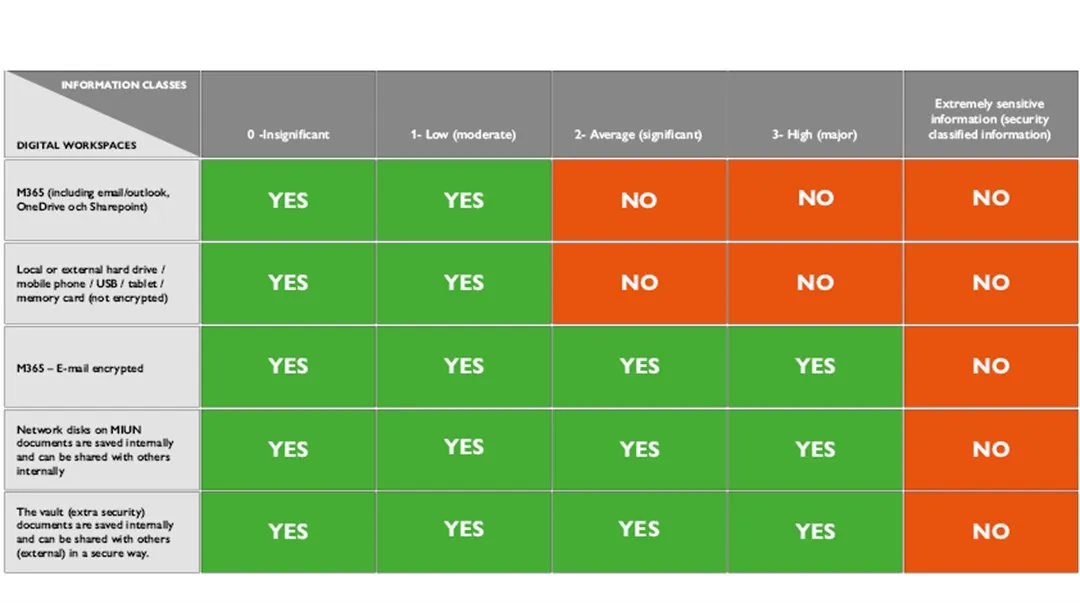
General guide for Mid Sweden University's approved digital workspaces
In the FAQ below "What information should you handle?" describes Mid Sweden University's approved storage areas to be used when the university is the information owner.
The choice of storage area must, among other things, be based on an information classification. One K-value (confidentiality) is linked to each type of information. The value is produced when the information classification is carried out (values of the information requirements for accuracy "R" and availability "T" are also produced during the information classification). The confidentiality value together with the value for accuracy and accessibility is also used to develop which security measures are required.
See more information on information security for further support or contact the Helpdesk if you are unsure how your information may be handled.
-
Text without personal data, confidentiality or security protection
A text without personal data, confidentiality or security protection. Even information with more harmless personal data, such data is either publicly available or not of a particularly private nature. eg name, position, contact information (phone number, email) for the job and similar work-related information.
K-value: 0-1
The following storage areas are approved
Mid Sweden University's internal workspacesCloud-based services at Microsoft, ex. OneDrive, SharePoint and Teams
E-mail transmission (Outlook, located in the cloud)
-
Information that contains sensitive or extra personal data worthy of protection
Sensitive personal data refers to data on:
- ethnic origin
- political opinions
- religious or philosophical belief
- membership in a trade union
- health
- a person's sexual life or sexual orientation
- genetic data
- biometric data
Sensitive personal data should generally not be processed at all, unless an exception can be found.
By extra personal data worthy of protection is meant data of a personal nature or that are close to private life, examples can be information about income or debts, grades, social security numbers, valuing information or the like.
Here is more information about handling personal data
Keep in mind!
Processing of data that includes crime or criminal suspicion has its own rules and should not be performed without appropriate protective measures.
K-value: 2-3The following storage areas are approved
Mid Sweden University's internal workspaces
Mid Sweden University vault (the vault)
Encryption
Information can be sent by e-mail if the encryption option is used, otherwise no.
Guides that show how to encrypt an email message
-
Information that may be classified
Confidentiality decisions shall be based on an assessment of the circumstances of the individual case. Here is a list of the areas that can more typically be covered by secrecy in our business. All information that can be included under these headings does not have to be confidential. In case of doubt, a lawyer should be consulted.
- Information about an individual's personal circumstances, Chapter 21 OSL
- Health and sexual life, Chapter 21, Section 1 OSL
- Persecuted persons, Chapter 21, Section 3 OSL
- Protected population registration, Chapter 21, Section 3a
- Processing in violation of the data protection regulation, Chapter 21, Section 7
- Research collaboration, Chapter 24, Section 5 OSL
- Commissioned activities, Chapter 31, Section 12 OSL
- Statistical secrecy, Chapter 24 Section 8 OSL
- Confidentiality in educational activities, Chapter 23, Sections 5 and 6 of the OSL
- Basis for knowledge tests / examinations, Chapter 17, Section 4
- Personnel administrative activities, ch. 39
- Procurement secrecy, Chapter 19 3 6 2 paragraph OSL
- Individual business relationship with authority, Chapter 31, Section 16 OSL
K-value: 2-3The following storage areas are approved
Mid Sweden University's internal workspaces
Mid Sweden University vault (the vault)
Encryption
Information can be sent by e-mail if the encryption option is used, otherwise no.
Guides that show how to encrypt an email message
-
Information covered by security protection
Information covered by security protection (espionage, national security secrecy, terrorism).
This type of information may not be stored on Mid Sweden University's computers, networks and external services. If there is a need to handle this type of information, a special investigation must be made, contact the information security coordinator in the infrastructure department (INFRA).